in this post we will have our look on how a Man In The Middle (MITM) attacks can be performed over SSL and TSL encrypted data transfer. The attack uses SSL strip developed by Moxie Marlin Spike with a ARP spoofing tool and a packet sniffer. The attack can be exclusively performed from UNIX and Linux based platforms hence I suggest you to use Dsniff. Practically SSL strip was developed to demonstrate how an attacker can lead visitors to visit his/her site from legitimate site. The attack used misinterpretation of null characters vulnerability which existed in several certificates during 2009.
I think its not good to demonstrate how attack can be performed since Moxie Marlin Spike has already provided a nice tutorial on his own website with a video.
Click this link
thoughtcrime.org to have a look on tutorial.
Here we gonna discus scene behind attack means why this attack is possible. Following figure demonstrates what happens when your data gets encrypted before it reaches its destination.
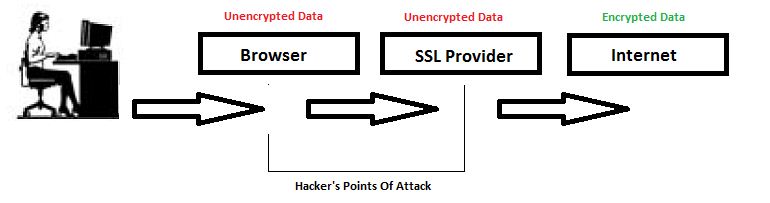
As you can see first of all your data goes to the CA authorities (SSL provider) for verification and then actual key exchange takes place, the scenario remains as it is even in LAN. Therefore if an attacker manages to fake out as CA authority it can sniff encrypted connection.
How attacker manages to fake out as authority?
1.First the attacker needs that all traffic in network should pass from his/her system.
2.So he/she performs ARP poisoning attack. (for more info on ARP poisoning read Packer Sniffer section).
3.Now he/she installs SSL strip in his/her system with respect to access point of network.
4.By doing so attacker manages to act as CA authority for all traffic that will pass from his/her system.
What goes behind the scene?
When victim tries to connect remote system using SSL connection. It asks for trust from a CA authority
and when it asks for trust to authority, SSL strip (which is installed in attacker's system) manages to reply with positive response. The SSL strip grants permission for connection using null-termination certificate and it guarantees attacker that the connection will just appear as HTTPS but all data transfer will be done using HTTP. Note that connection would be HTTPS but work as HTTP since null certificate does not provide any security and attacker will successful sniffing packets from SSL connection.
The best countermeasure I can suggest over this kind of attack is installing anti-sniffing and arp spoofing detection tools. And for clients in LAN never ever trust any connection that you would be making from your LAN network.
 Tue Apr 28, 2015 9:35 am by THE-OUTSIDER
Tue Apr 28, 2015 9:35 am by THE-OUTSIDER

