Desktop Phishing is an advance form of phishing attack. In a simple
Phishing Attack . The attacker convinces the victim to click on a link which contains a fake login page,Victim then enters his credentials such as user names passwords in the fake login page that goes to the attacker. Victim is then redirected to an error page or genuine website depending on the attacker. But the main drawback in this
Phishing Attack is the victim can easily differentiate between fake and real login page by looking at the URL which contains a different domain name. We can overcome this in desktop phishing by spoofing the domain name
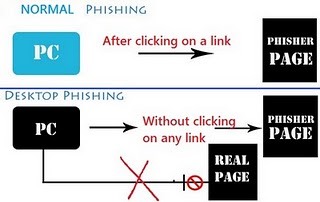
In Desktop Phishing The Attacker just replaces some text in the hosts file which is located in Windows directory of the victims computer. The attacker does this by sending a executable or a batch file and convinces the victim to click it, Now whenever the victim visits the real website like paypal.com He is redirected to the attackers phishing page But the domain name (paypal.com) remains the same as typed by the victim and the victim doesn't come to know that it is a fake page, Thus this type of phishing attack has very good success rate.
I Hope this helped You so far.. If You haven't Read Our Previous Posts On Phishing
Tab Napping (-Video Included)Simple Phishing Attack
 Tue Apr 28, 2015 9:35 am by THE-OUTSIDER
Tue Apr 28, 2015 9:35 am by THE-OUTSIDER


